In this post I’ll explain how to detect an attacker that uses PsExec to connect to your computer when you don’t have visibility over the attacker’s computer.
Note: In this post I use Logz.io for my examples, but I recently switched to Humio. For more details: https://www.tristandostaler.com/why-i-switched-from-logz-io-to-humio/
For this post, I assume you’ve read my SIEM 100 series where I explain the basics of Logz.io. I’ll be using the stack I created in this series to demonstrate what to do.
PsExec is a tool provided by Microsoft in the Sysinternals suite: https://docs.microsoft.com/en-us/sysinternals/downloads/psexec
Like they explain:
PsExec is a light-weight telnet-replacement that lets you execute processes on other systems, complete with full interactivity for console applications, without having to manually install client software. PsExec’s most powerful uses include launching interactive command-prompts on remote systems and remote-enabling tools like IpConfig that otherwise do not have the ability to show information about remote systems.
https://docs.microsoft.com/en-us/sysinternals/downloads/psexec
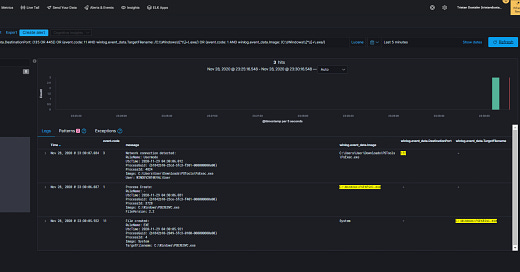
PsExec can be use as an adversary to pivot between computers and/or elevate privileges. It is rather easy to detect when executed on a monitored endpoint, but what happens when a remote computer not monitored use it to connect to a monitored endpoint?
It turns out it can be detected by looking for a chain of 3 events, distinctive of PsExec behavior when remote connecting.
Keep reading with a 7-day free trial
Subscribe to Tristan’s Cybersecurity Substack to keep reading this post and get 7 days of free access to the full post archives.