Zero Trust Architecture – What it is and what I think of it
I have been reading the Zero Trust Architecture (ZTA) publication from the NIST for quite some time now. You can find the document here: https://csrc.nist.gov/publications/detail/sp/800-207/final. This 41 page document is dense and full of advanced architecture patterns. It took me a while to read and understand.
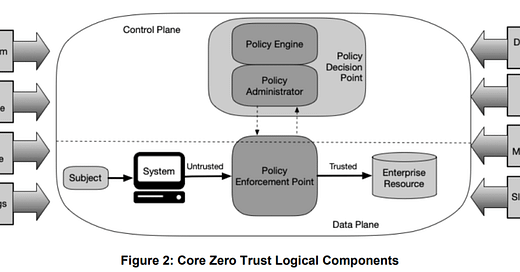
What is a Zero Trust Architecture
A Zero Trust Architecture (ZTA) is an Information Security architecture based on the idea that a network shouldn’t have inherent trust on the internal boundary. Many enterprise networks are designed like an egg where they have a rather strong and robust external shell, but once inside the shell, everything is lax; it needs only a little needle that is able to break through the shell to wreak havoc inside.
Keep reading with a 7-day free trial
Subscribe to Tristan’s Cybersecurity Substack to keep reading this post and get 7 days of free access to the full post archives.